Difference between revisions of "Remote Access"
| Line 1: | Line 1: | ||
| + | ==Introduction== | ||
| + | Monitoring stations will by necessity be out in the weather, which requires that they be sealed from the elements. However, this makes them difficult to access if you want to make any changes to the software or just log in to check on things. Breaking open the sealed container runs the risk of compromising its integrity, and is a time-consuming pain besides. The following sections will cover ways to access your HiveTool remotely. | ||
| + | |||
| + | ===Assumptions and Configuration=== | ||
| + | The following discussion assumes you're using a Raspberry Pi with the 0.8.4 release of HiveTool software. It also assumes minimal experience with Linux and is targeted primarily at Windows users. | ||
| + | |||
| + | ==Remote Access on a Local Network== | ||
| + | The HiveTool program typically assumes access to an internet connection to perform basic functions, like coordinate time with NIST servers and upload data to the HiveTool.net site. While some installations will be entirely wired by ethernet cables, the typical somewhat remote placement of apiaries means there will likely be a wireless connection involved. Wired or wireless, if you have access to the same router that the HiveTool is connecting to the Internet through, you can access it through that connection | ||
| + | |||
| + | ===PuTTY=== | ||
| + | If you're comfortable with a Command Line Interface (CLI), by far the easiest method it to use Secure SHell (SSH) connections. If using a Windows machine to connect to a Linux operating system like the Raspbian OS on a Raspberry Pi, the most common software is [https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html PuTTY] | ||
| + | |||
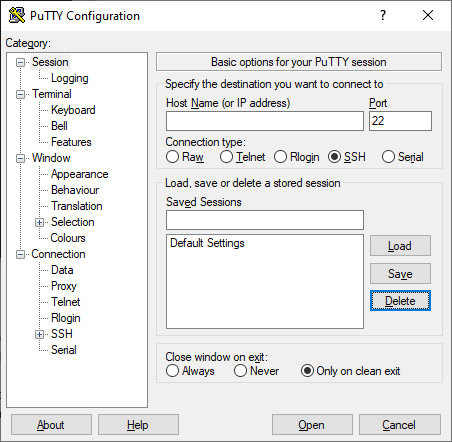
| + | After downloading and installing PuTTY, when you run it you should see a page similar to the following: | ||
| + | |||
| + | [[File:PuTTY.png]] | ||
| + | |||
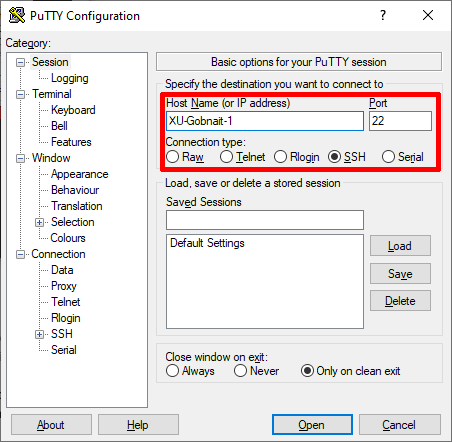
| + | Notice that the '''SSH''' connection type is already selected and the Port defaults to 22. You should not have to change these settings. If the computer you are using is connected to the same network that the Pi is using (i.e. they're all on the same ''Local'' network), you can enter its hostname and click "Open" to start a secure shell session: | ||
| + | |||
| + | [[File:PuTTY_login.png]] | ||
| + | |||
| + | Note that your hostname will be whatever is set for your Raspberry Pi and will almost certainly not match what is shown above. If you know the IP address the HiveTool is using you can also connect to it using that, though the hostname is usually simpler as it will find the device even if it's IP has changed (as most devices are assigned IPs dynamically and change periodically). If you don't know what hostname your HiveTool is using or you want to change it to something else, check the [[Change_Hostname]] page. | ||
| + | |||
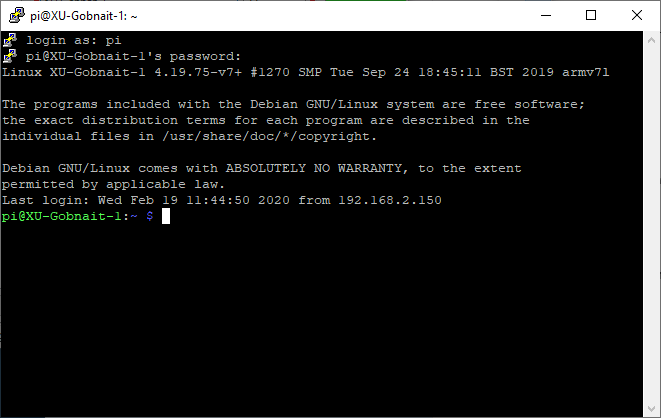
| + | You will then be prompted to log in to your HiveTool. You should have been given a user name and password with your installation, or else have set it yourself; in most cases the default user of '''pi''' is used. | ||
| + | |||
| + | [[File:SSH_login.png]] | ||
| + | |||
| + | You are now in a typical terminal session and can execute commands as normal. However you will most likely not be able to use the desktop interface unless you're willing to go through extra work configuring PuTTY to handle it. For cases requiring the GUI, VNC or XRDP will likely be easier. | ||
| + | |||
| + | ==Remote Access from a Non-Local Network== | ||
| + | |||
This will allow remote access to the hive computer without opening any ports on the router using reverse IP tunneling. | This will allow remote access to the hive computer without opening any ports on the router using reverse IP tunneling. | ||
Revision as of 09:18, 19 February 2020
Contents
Introduction
Monitoring stations will by necessity be out in the weather, which requires that they be sealed from the elements. However, this makes them difficult to access if you want to make any changes to the software or just log in to check on things. Breaking open the sealed container runs the risk of compromising its integrity, and is a time-consuming pain besides. The following sections will cover ways to access your HiveTool remotely.
Assumptions and Configuration
The following discussion assumes you're using a Raspberry Pi with the 0.8.4 release of HiveTool software. It also assumes minimal experience with Linux and is targeted primarily at Windows users.
Remote Access on a Local Network
The HiveTool program typically assumes access to an internet connection to perform basic functions, like coordinate time with NIST servers and upload data to the HiveTool.net site. While some installations will be entirely wired by ethernet cables, the typical somewhat remote placement of apiaries means there will likely be a wireless connection involved. Wired or wireless, if you have access to the same router that the HiveTool is connecting to the Internet through, you can access it through that connection
PuTTY
If you're comfortable with a Command Line Interface (CLI), by far the easiest method it to use Secure SHell (SSH) connections. If using a Windows machine to connect to a Linux operating system like the Raspbian OS on a Raspberry Pi, the most common software is PuTTY
After downloading and installing PuTTY, when you run it you should see a page similar to the following:
Notice that the SSH connection type is already selected and the Port defaults to 22. You should not have to change these settings. If the computer you are using is connected to the same network that the Pi is using (i.e. they're all on the same Local network), you can enter its hostname and click "Open" to start a secure shell session:
Note that your hostname will be whatever is set for your Raspberry Pi and will almost certainly not match what is shown above. If you know the IP address the HiveTool is using you can also connect to it using that, though the hostname is usually simpler as it will find the device even if it's IP has changed (as most devices are assigned IPs dynamically and change periodically). If you don't know what hostname your HiveTool is using or you want to change it to something else, check the Change_Hostname page.
You will then be prompted to log in to your HiveTool. You should have been given a user name and password with your installation, or else have set it yourself; in most cases the default user of pi is used.
You are now in a typical terminal session and can execute commands as normal. However you will most likely not be able to use the desktop interface unless you're willing to go through extra work configuring PuTTY to handle it. For cases requiring the GUI, VNC or XRDP will likely be easier.
Remote Access from a Non-Local Network
This will allow remote access to the hive computer without opening any ports on the router using reverse IP tunneling.
NOTE THAT THIS WILL ONLY WORK IF YOU HAVE ACCESS TO THE HIVETOOL DATABASE!
Create an automatic login from pi@hive_computer to user@target_host
http://www.linuxproblem.org/art_9.html
On hive_computer, as pi, generate the key: sudo ssh-keygen -t rsa
# ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: d9:2e:40:2d:59:b1:6e:f2:08:7e:6a:3e:96:2e:bf:04 root@NAPAPi5 The key's randomart image is: +---[RSA 2048]----+ | o. | | + . | | + o | | . o o | | E . o S . | | o . * . | | o.o o . | | ..=o . | | B*o | +-----------------+
append it to target_host's authorized_keys
cat .ssh/id_rsa.pub | ssh -pTARGET_PORT pi@TARGET_IP 'cat >> .ssh/authorized_keys'
where
TARGET_PORT is target_host's ssh port, if use, like 8022 TARGET_IP is target_hosts ip, like 192.168.254.12
Make hive_command.pl executable:
sudo chmod a+x hive_command.pl